How Easy is it For Someone to Steal Your Identity?

Credit: danijelala
How often have you clicked a link online, especially on social media? You’ve probably lost count.
Me too.
But clicking one URL cost me nearly $6,000 in 2013. It was supposed to be a YouTube link to watch the recap of the Super Bowl XLVII between the 49ers and the Ravens.
The 49ers lost, which hurt, but I had no idea another heartbreak would come from the URL I clicked.
Unfortunately, it was a phishing link that installed spyware on my device. It resulted in hackers accessing my personal and financial information.
My decision to click a bogus URL cost me a lot of money. But sometimes, it’s not always the victim’s fault.
For example, my cousin Jack became an identity theft victim after a data breach on his father’s employer. His personal details were listed in the HR database for insurance purposes.
After the breach, his dad didn’t take any security measures to protect the compromised data. And his information was used to defraud a college of more than $7,000.
You see, it’s quite easy for someone to steal your identity. That’s because the world has gone digital, and scammers now use sophisticated tools.
There are many trivial things we do online that are overlooked. For example, connecting to public Wi-Fi, posting pictures on social media, and revealing sensitive details about ourselves during the “talking stage.”
Most of us have normalized these everyday actions. But they’re part of the many ways scammers can use to commit fraud. And by doing these things, we’re making it easy for them to steal our identity.
But don’t be deceived; the internet isn’t the only place where someone can steal your identity.
Old-school strategies like dumpster diving, tailgating, and eavesdropping still work.
Fraudsters have also become creative in their social engineering tactics.
Add that to the latest sophisticated tools and software they use. And you’ll see how easy it is to become an ID theft victim.
As a previous identity theft victim, I’ll discuss the “little things” we do that can lead to big consequences, such as exposing us to identity theft. I’ll also mention how to protect yourself physically or online.
Remember, the devil is in the details.
How Can Someone Steal Your Identity?
There are many things you can do to make it easy for someone to steal your identity.
Most times, we’re oblivious to them.
Your first line of defense against identity theft is your behavior. What you do can make it significantly easy or practically impossible for scammers to get your information.
In the following paragraphs, you’ll find different actions that expose you to identity theft.
1. Using Public Wi-Fi
Public Wi-Fi is free, so many people love it. But so do hackers.
I generally don’t use public Wi-Fi and advise people not to.
However, we sometimes can’t help ourselves. You could be at the airport waiting for hours or at a coffee shop and want to browse something quickly.
Unfortunately, free Wi-Fi isn’t secure. It doesn’t matter if it requires a password; you’re risking your money and identity.
If you must use public Wi-Fi, here are ways to keep your data safe:
Ensure the Firewall is Active
Firewalls can protect your device from hackers attempting to access your data by alerting you to suspicious websites and files.
Remember to turn the firewall on before connecting to public Wi-Fi.
Use Anti-Virus Software
Installing anti-virus software protects your devices from malware, hackers, ransomware, and phishing. It runs in the background providing real-time protection without interfering with your internet use.
Some of the best anti-virus software include McAfee, Norton 360, Bitdefender, and IDShield.
Turn Automatic Connectivity Features Off
Turn off any feature that allows automatic connection with other devices or public wireless networks. For example, turn off Bluetooth, AirDrop, and Printer Sharing. In addition, ensure you “forget the network” after using public Wi-Fi.
Verify the Network and Turn Off the Sharing
Hackers often create fake networks, so always verify the network name before joining. If possible, ask a company employee if the link is genuine.
Make sure you turn off sharing preferences when connected to the public internet.
Use a VPN
A VPN (Virtual Private Network) allows you to browse the internet anonymously by routing your web activities through an encrypted server.
If you’re always on the road and use public transport, ensure you install a good VPN. There are many options but paid VPN services are more secure and reliable than free ones.
A strong VPN only costs a few bucks per month, which is a wise investment considering the dangers it’ll save you from.
Some examples are NordVPN, Private Internet Access, Surfshark, Norton from LifeLock, and Hotspot Shield.
Look Out for the HTTPs Padlock
Whether or not you’re connected to a public network, ensure the website you visit has the padlock icon to the left and the “s” for “secure” after “HTTP” in the web address.
Sites with HTTPS are more secure than HTTP because they use encryption to protect the data you send to the site’s server.
Don’t Input Personal Information on Sites You Visit
Typing personal information and login credentials while on public Wi-Fi is risky – even with HTTPS.
Don’t Download or Install Using Public Wi-Fi
Free Wi-Fi allows you to download all the movies you want to binge-watch.
But downloading something over public wireless networks is dangerous. Don’t click pop-up notifications asking you to install something.
This is also not the time to do system upgrades or updates.
2. Revealing Personal Information to Strangers
Don’t reveal personal information to strangers, especially people you’ve only met online.
Your name is the most common information used to identify you.
Protecting your name is almost impossible, except not disclosing it casually to just about anyone who asks. And quite frankly, simply knowing your name won’t help a thief steal your identity.
However, when you reveal other personally identifiable information (PII), like your address, phone number, age, and email address, you’re exposing yourself to identity theft.
Ensure you omit your address from social media posts and checks. For example, a check already has your name and bank account number. Adding your address makes it easy for someone to steal your identity.
Being careless with your email address can also expose you to phishing schemes. This happens when a scammer sends an email that looks like it’s from a credible source and urges you to click a link to log into your account.
Doing this will expose your login credentials to the scammer.
3. Exposing Your Social Security Number (SSN)
Your SSN is probably the most valuable information that shouldn’t get into the wrong hands.
When the personally identifiable information I mentioned above and an SSN are combined, the results can be disastrous.
Identity thieves can use your SSN to obtain credit in your name.
The best way to protect your SSN is not to carry your Social Security Card everywhere you go.
Also, be careful when sharing your number. Even when asked for it, ask why they need your number, how it’ll be used, and what happens if you refuse.
But your Social Security Card isn’t the only sensitive document you shouldn’t routinely carry.
4. Carrying Sensitive Documents With You Everywhere
Carrying personal papers with you every time makes it easy for someone to steal your identity.
Your wallet or car’s glove compartment isn’t a safe place to keep your birth certificate, driver’s license, passport, or other sensitive documents.
Since official documents had my photo on them, I used to think they were useless to anybody.
But scammers have become creative and have a slew of software.
These documents can be edited and used to impersonate you.
It’s almost impossible to prove your innocence when personal documents like a passport or driver’s license are connected to a crime.
Keep the original and its copies in a safe – or somewhere it can’t be accessed easily.
Be extremely cautious when disclosing the information, especially if doing so requires physically handing the document to the other party.
If any of these documents ever go missing, report to the local police department immediately. The copies will help you provide important information to support the loss.
✎ Related: What Can Someone Do With Your Driver’s License Number?
5. Sharing Pictures to Social Media
We’re all guilty of sharing pictures on our social media.
It’s okay to keep up with your friends and family online. But with every new information or picture you add to your social media profile, you’re increasing the chances of becoming an identity theft victim.
The social media frenzy can make people overshare information or photos that should be kept private.
Here are some reasons why your social media pictures make it easy for someone to steal your identity:
To protect yourself, remove geotagging from pictures before posting, and don’t share high-resolution images.
Don’t expose your kids and resist the urge to join viral challenges that involve divulging personal information – not even your high school.
There are more safety precautions for using social media. Read my complete guide on the dangers of posting your pictures online and how to protect yourself.
6. Not Shredding Physical Documents Before Disposal
Identity theft isn’t always perpetrated through the internet.
While protecting your social media and online activity, you could still become an identity theft victim.
That’s why you shouldn’t forget the basics.
Shred any documents containing personal information before disposing of them. This includes bank statements, IRS correspondence, and credit card reports.
Once you take the trash out, you have no idea what happens after. So, ensure that all documents are useless to anyone digging into the trash can.
7. When You’re a Data Breach Victim
Data breaches are happening at an unprecedented rate – around 2,200 attacks daily.
This would normally not bother me because it’s the company’s problem. But not when your information is involved.
Most cyber-attacks happen because scammers are trying to access the sensitive information you gave these companies.
If a service you use has experienced a data breach recently, find out if your records were affected.
Organizations are typically required to announce cybersecurity attacks when they happen.
So, if you were affected, here’s how to protect yourself after a data breach:
Continue to monitor your credit and financial health. Report any suspicious activity to local authorities. If you suspect you’ve been a victim before taking these measures, immediately report identity theft to the FTC.
8. Not Protecting Your Desk at Work
Now, I don’t want you to be paranoid.
But it’s important to be safety-conscious even at work.
If you use your private data while working, ensure they aren’t exposed on your desk.
Avoid leaving documents open on the desk or confidential information on your screen, especially when you’re not in your seat.
A clean desktop policy isn’t only good for you.
People working in the same organization don’t always have the same information privileges.
So, protect other people’s sensitive information from unauthorized access.
Shredding sensitive documents also applies here. Don’t just rumple and throw them into the bin.
9. When Someone Around You Has Recently Been an ID Theft Victim
Has a friend or family member been an identity theft victim? Or maybe their information was leaked during a data breach.
DON’T OVERLOOK IT.
My cousin Jack’s personal information was stolen after his dad’s employer database was attacked. He was listed in the company’s HR files for insurance coverage.
You don’t know how much information a friend, family member, or neighbor has about you.
If they mention an attack on them, treat it like you were the victim.
10. If Your Parent Has a Homecare Attendant
Besides kids, elders are the most exposed demographic to identity theft. Between 2017 to 2021, elder fraud loss increased by 391.9%.
The likelihood of your parent or senior family member being a fraud victim is also high because they’re less likely to report the incident.
As such, your elderly parent could be at risk of identity theft if they’re being cared for by a homecare attendant or nurse.
Unfortunately, some of our sensitive records are often with our parents.
This means you’re also exposed to identity theft if the carer looks through their records for your information.
Read my guide on how you can protect seniors and the elderly from identity theft.
11. Not Using Strong Passwords
I mentioned this as part of security measures after a data breach or identity theft case.
But you shouldn’t wait till an incident happens before using strong and different passwords across your accounts, especially financial platforms.
As a rule of thumb, I ensure all passwords are at least 15 characters with a combination of numbers, letters, and symbols.
Hackers often use brute-force attacks to break weak passwords. They can use automated computer algorithms to try different combinations quickly.
Check out this quick infographic showing the time it takes for a hacker to brute-force your password:
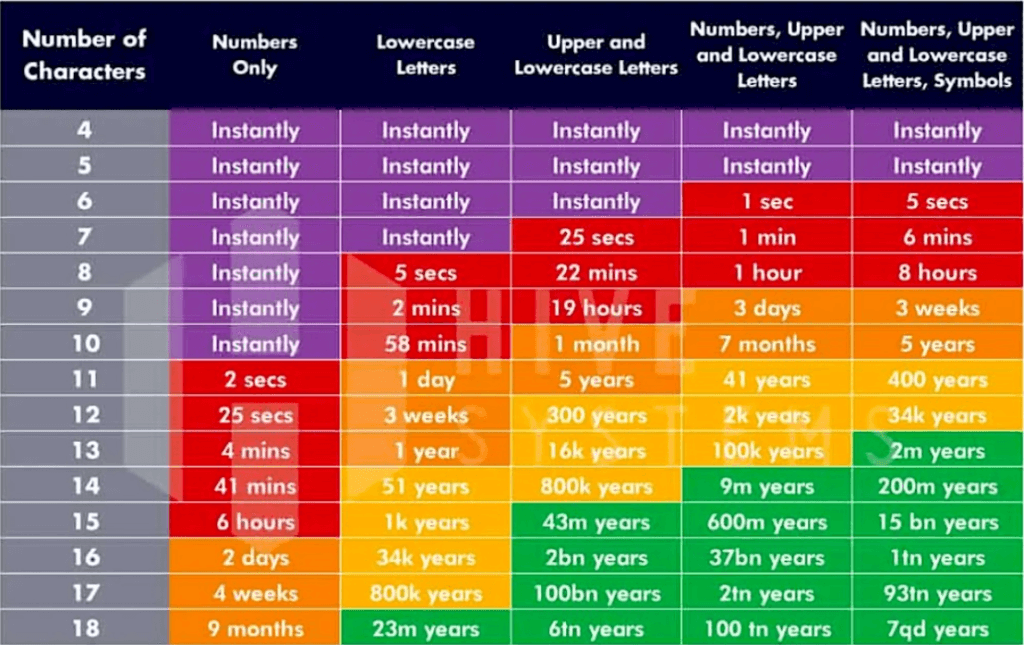
The chart of data sourced from HowSecureIsMyPassword.net
The longer your password is with different variations of an upper case letter, one symbol, and one number, the more difficult it is for a computer to crack.
✎ Related: How to Keep Your Passwords Safe from Hackers and Thieves ➔
Conclusion
It’s safe to say we are all guilty of virtually everything I discussed.
That means it’s quite easy for someone to steal your identity. Although you might not be able to control things like a data breach, you’re still the first line of defense against identity theft.
As such, what you do will significantly impact how easy it is for scammers to defraud you. Protect yourself online and physically.
Remember that scammers are getting creative by the day, plus they have a plethora of software to help them.
Be responsible for your actions online, and if you ever suspect you might be a victim, report it immediately to the Federal Trade Commission and local authorities.
Related Articles About Identity Theft:


